Manual on-boarding of users via email communication
The Hiring Manager, Human Resources (HR) team and Information Technology (IT) team are in constant email communication to ensure on-boarding process is done on time before employee joining date.
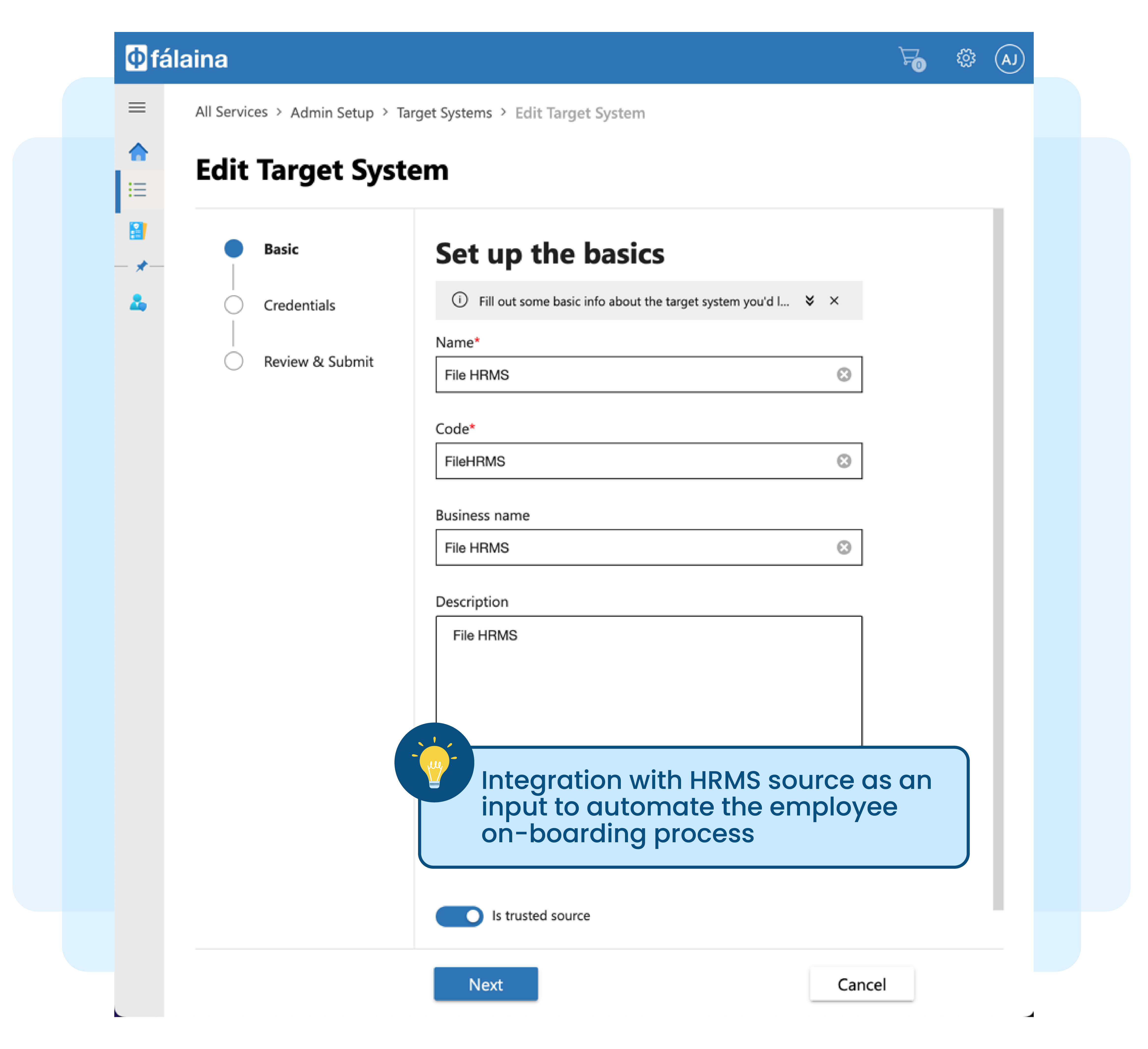
This on-boarding process includes:
- Entry into Human Resources Management Systems (HRMS)
- Passing of information from HR to IT
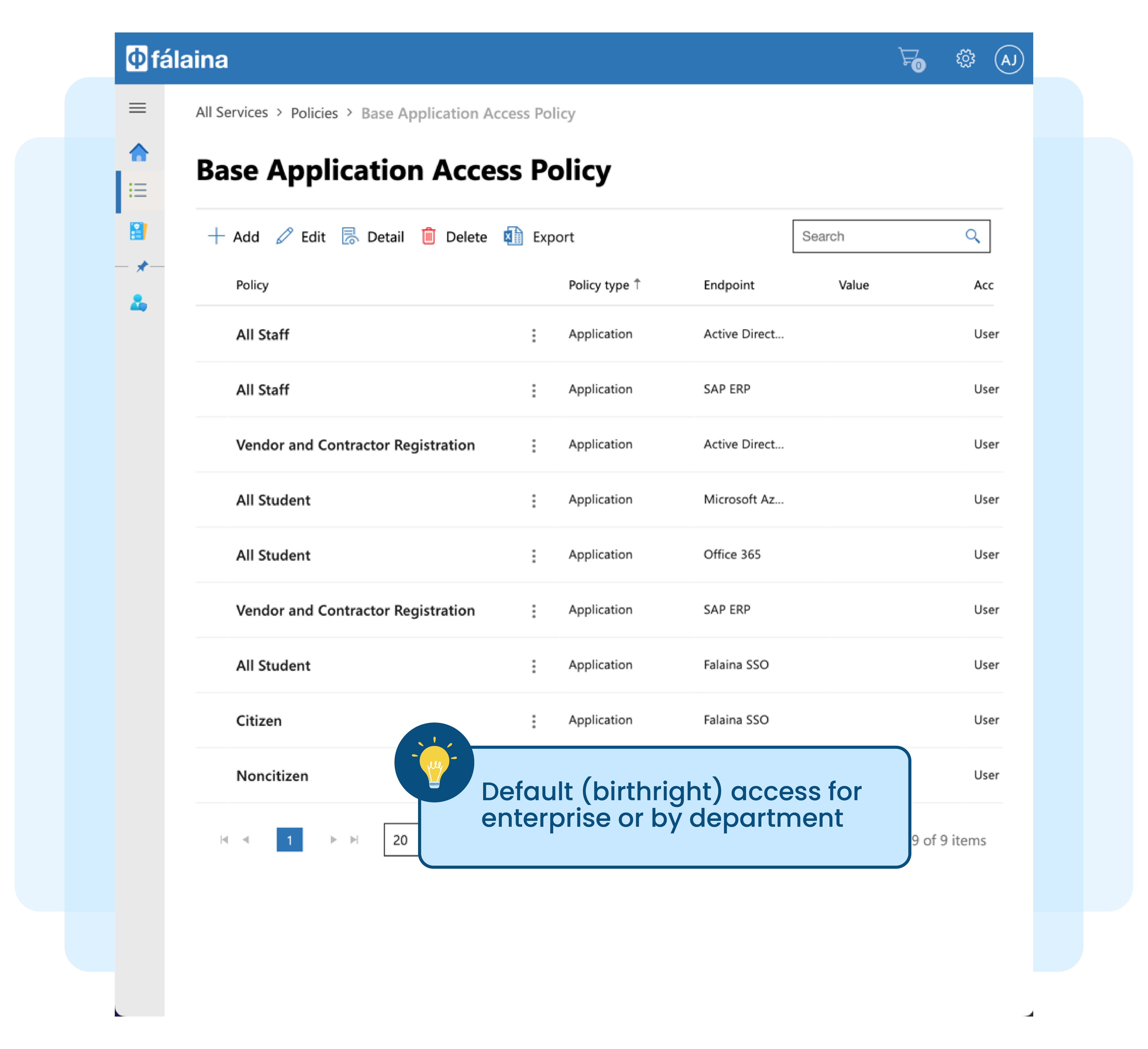
- Access to set of systems created by IT team, which is deemed as default access for all employees (i.e. network login, typically Microsoft Active Directory, and email system or employee portal)
Despite being the status quo, this method of manually sending emails with information to HR and then to IT team to create access is not practical as:
Sending email on required access for employees is not efficient and error-prone
Information may not be received on time and may be incomplete – required access may not be created on time
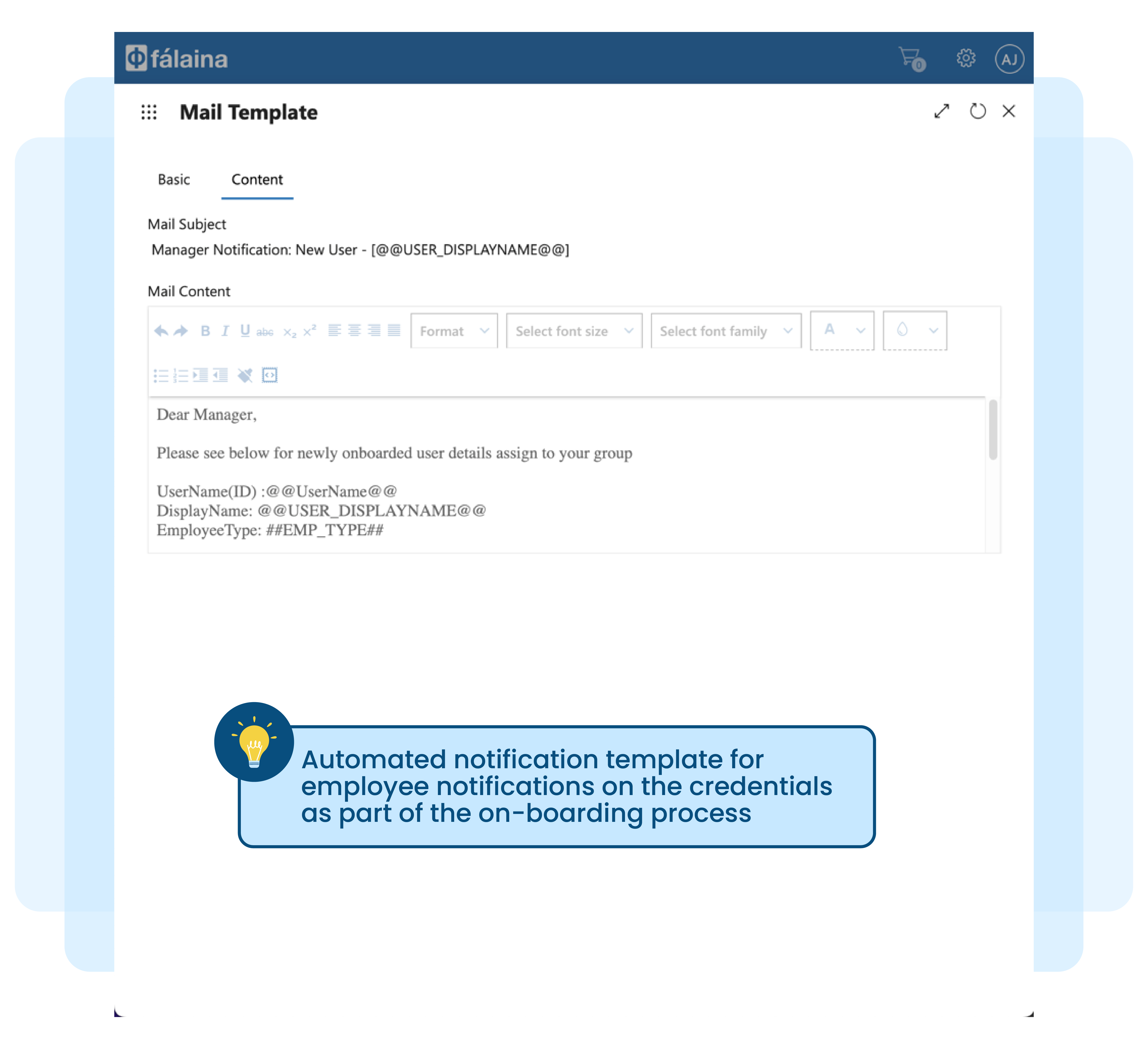
Sending confidential access credentials (ID and password) via email to managers or employees may not be safe
Employees may not be productive due to delay in access creation
Access may not be created appropriately – wrong or excessive access
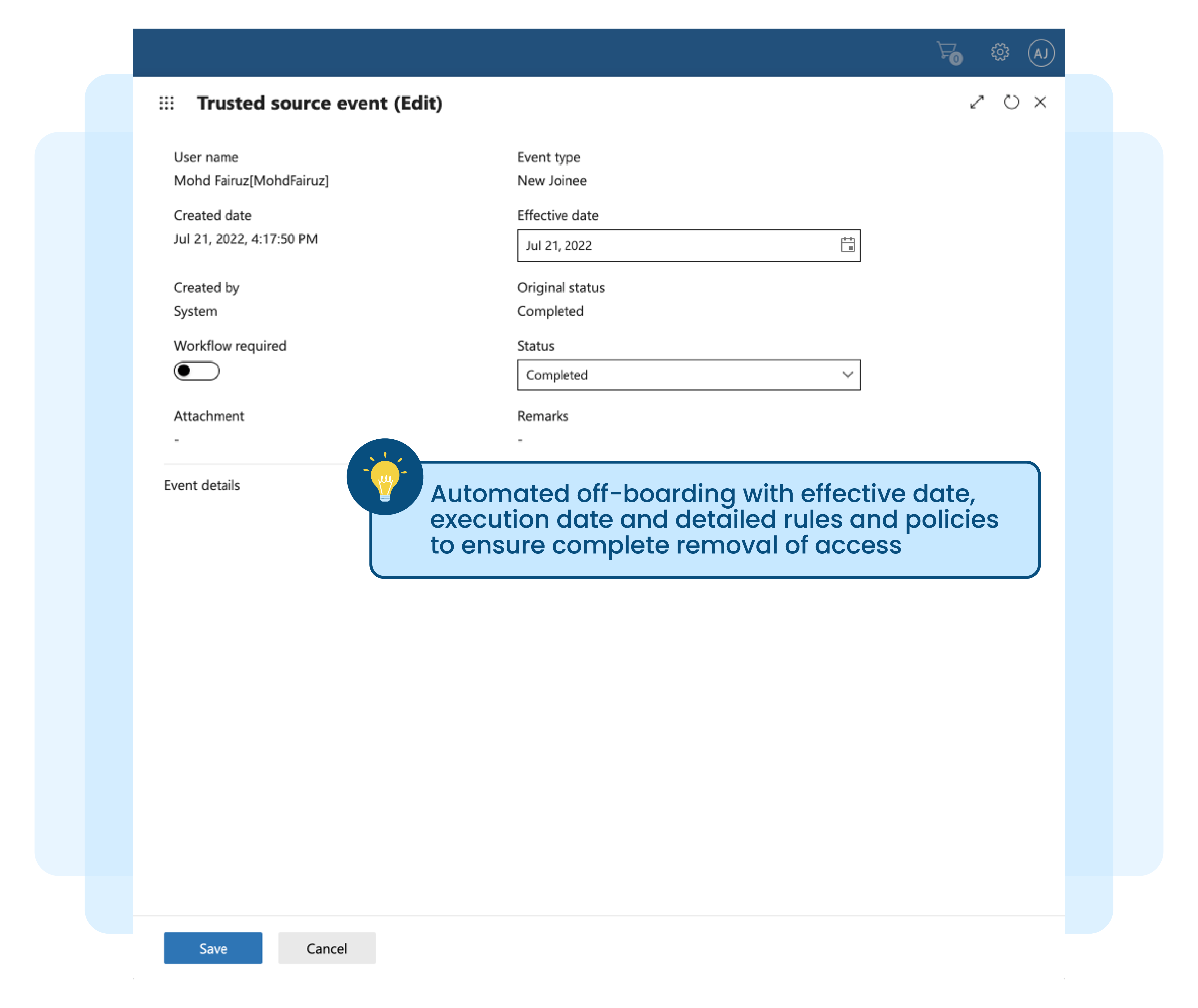
Manual off-boarding of employees without proper access record
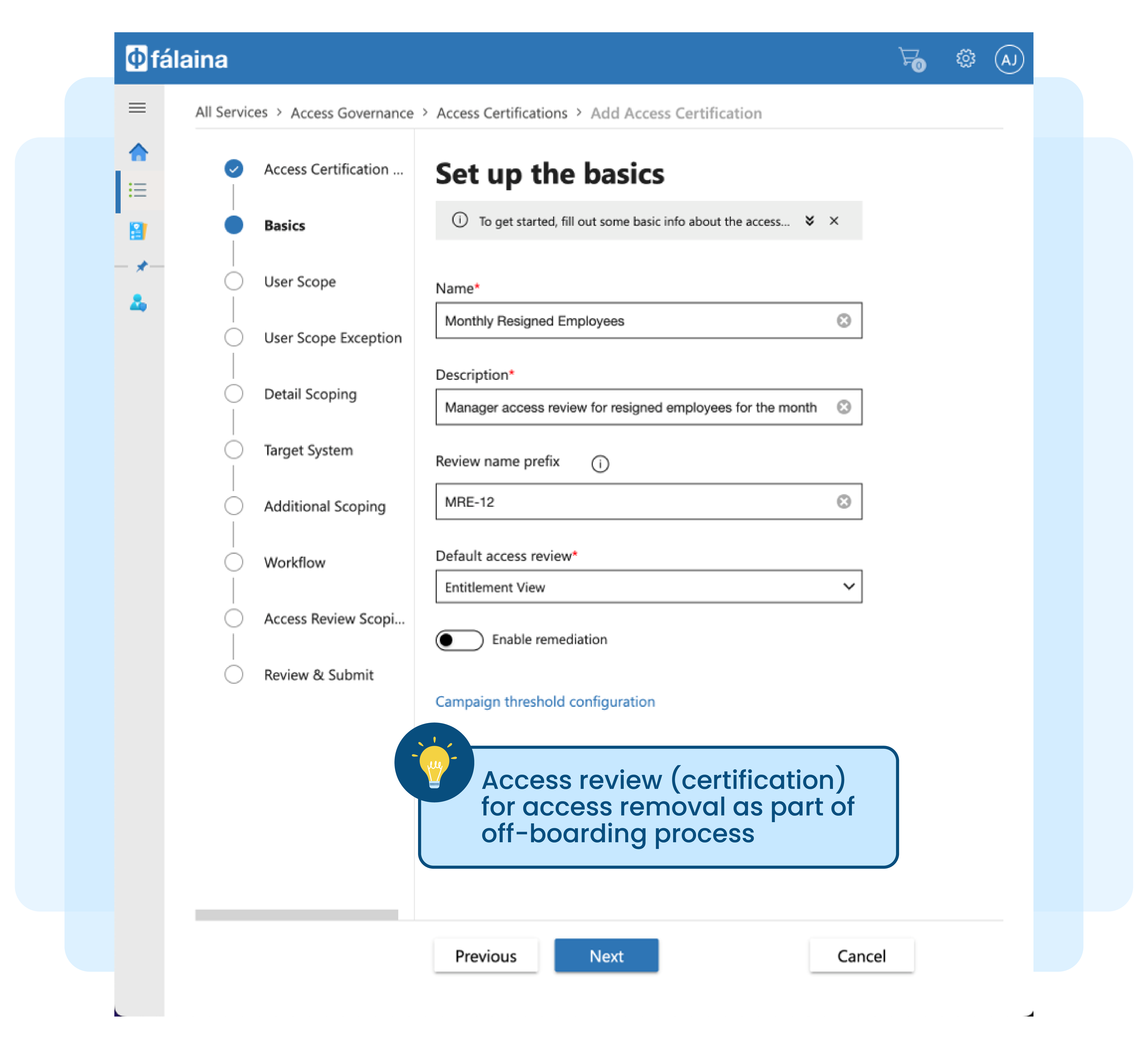
Off-boarding of employee access from enterprise applications and infrastructures poses a significant threat when no proper record is maintained for access issued from day one of employment to present. Access creep further adds to the complexity, which happens gradually and in an unmonitored way when granting permission to individuals or roles over an identity lifecycle.
Why manual removal of access right is not practical:
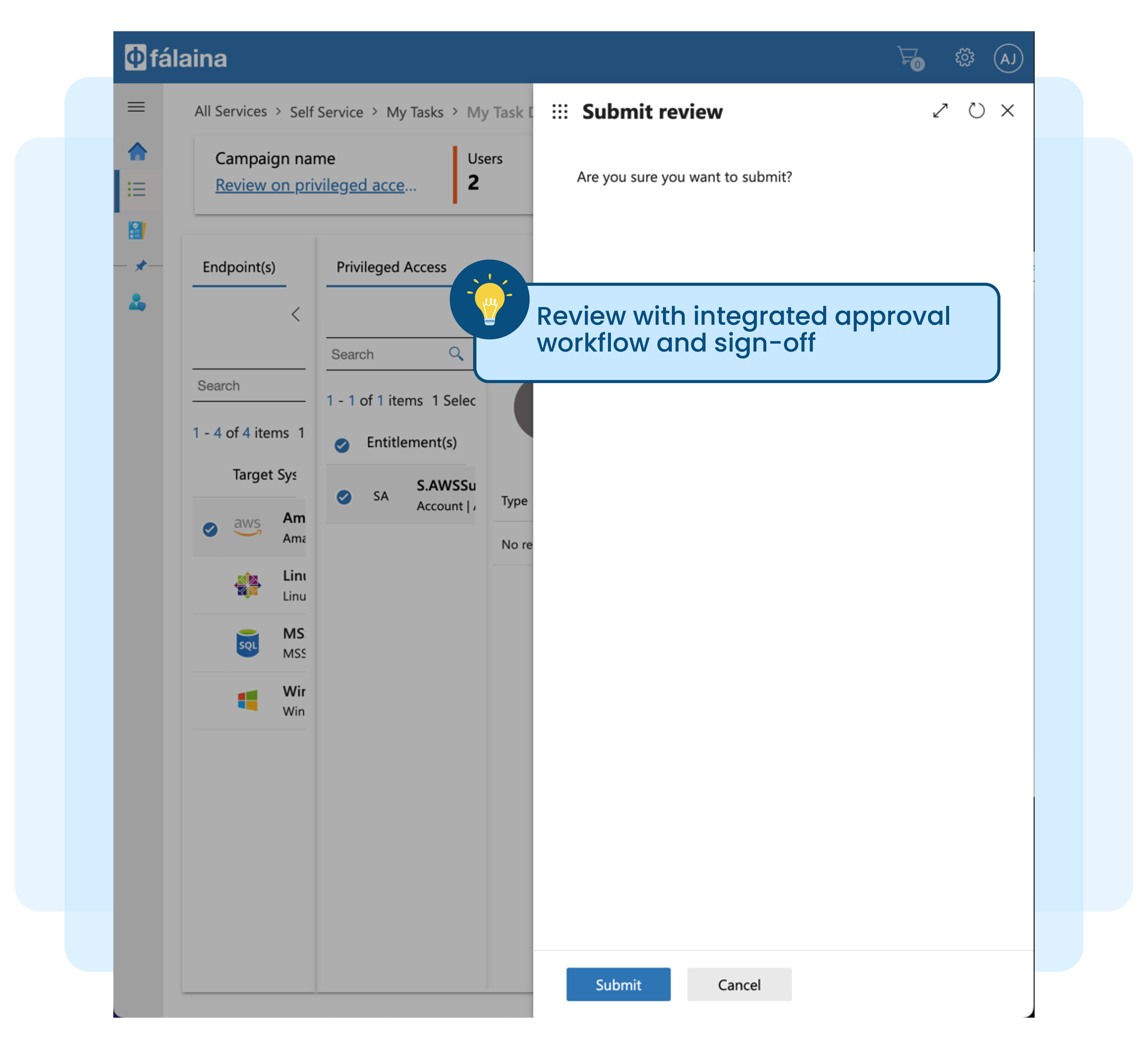
No access certification or rubber stamping of access removal during exit process
Removal of access rights may not be complete, especially when the user account and employee name are not similar in nature
Access cannot be removed in a timely manner, and some access may be left behind for many reasons
Risk of insider threat when other employees or managers take ownership of leavers' accounts
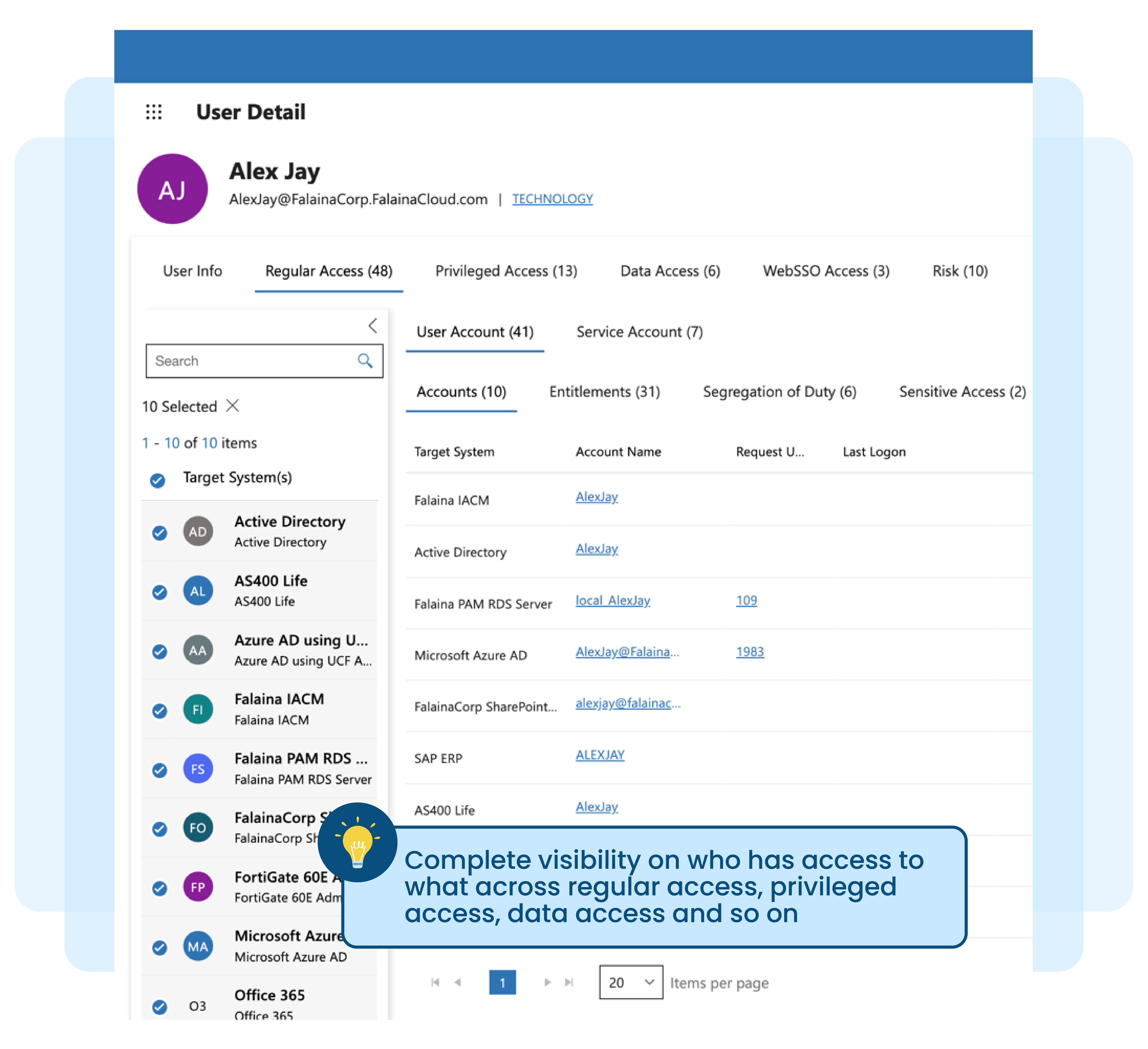
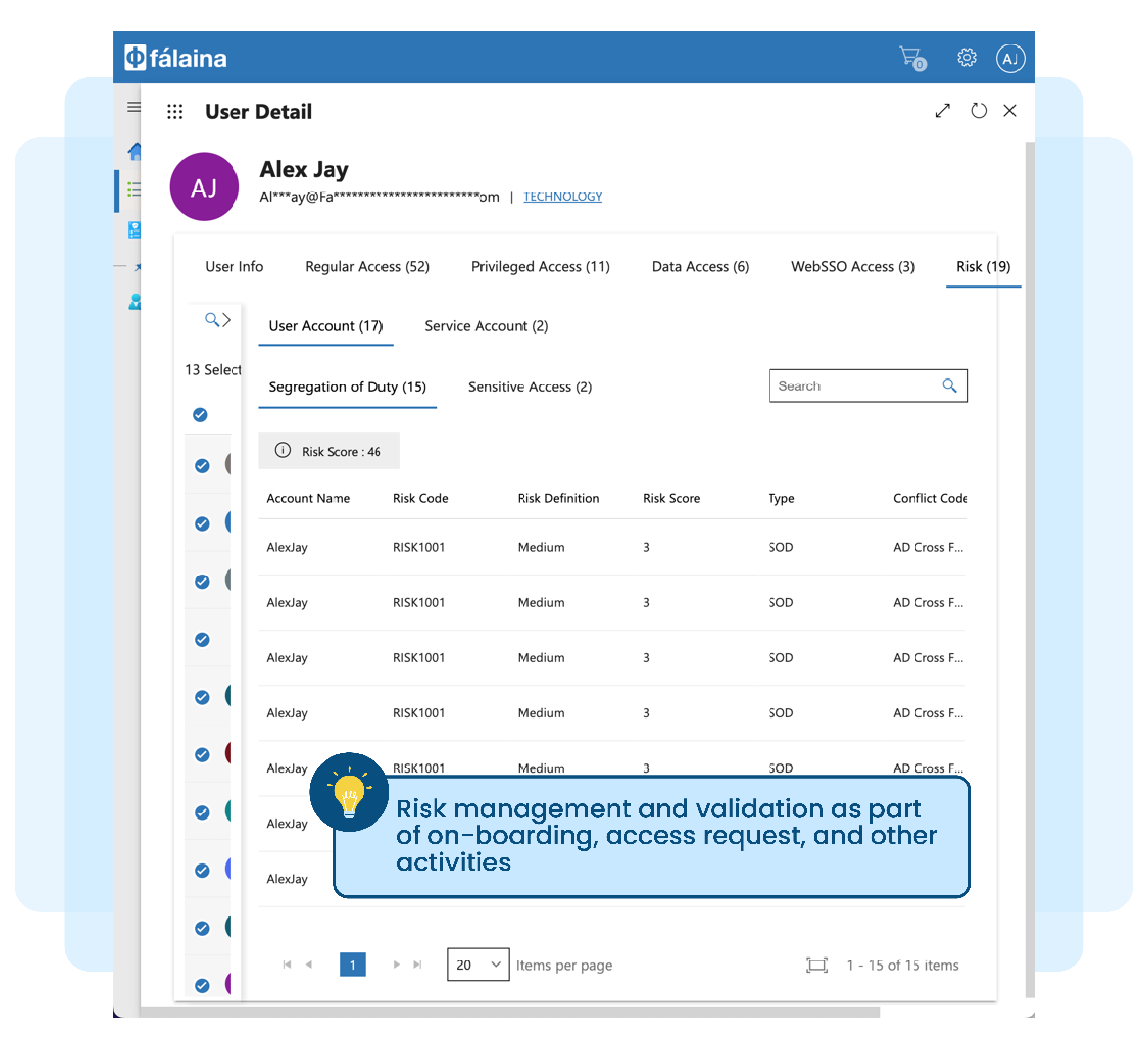
Spread-sheet based manual access right review
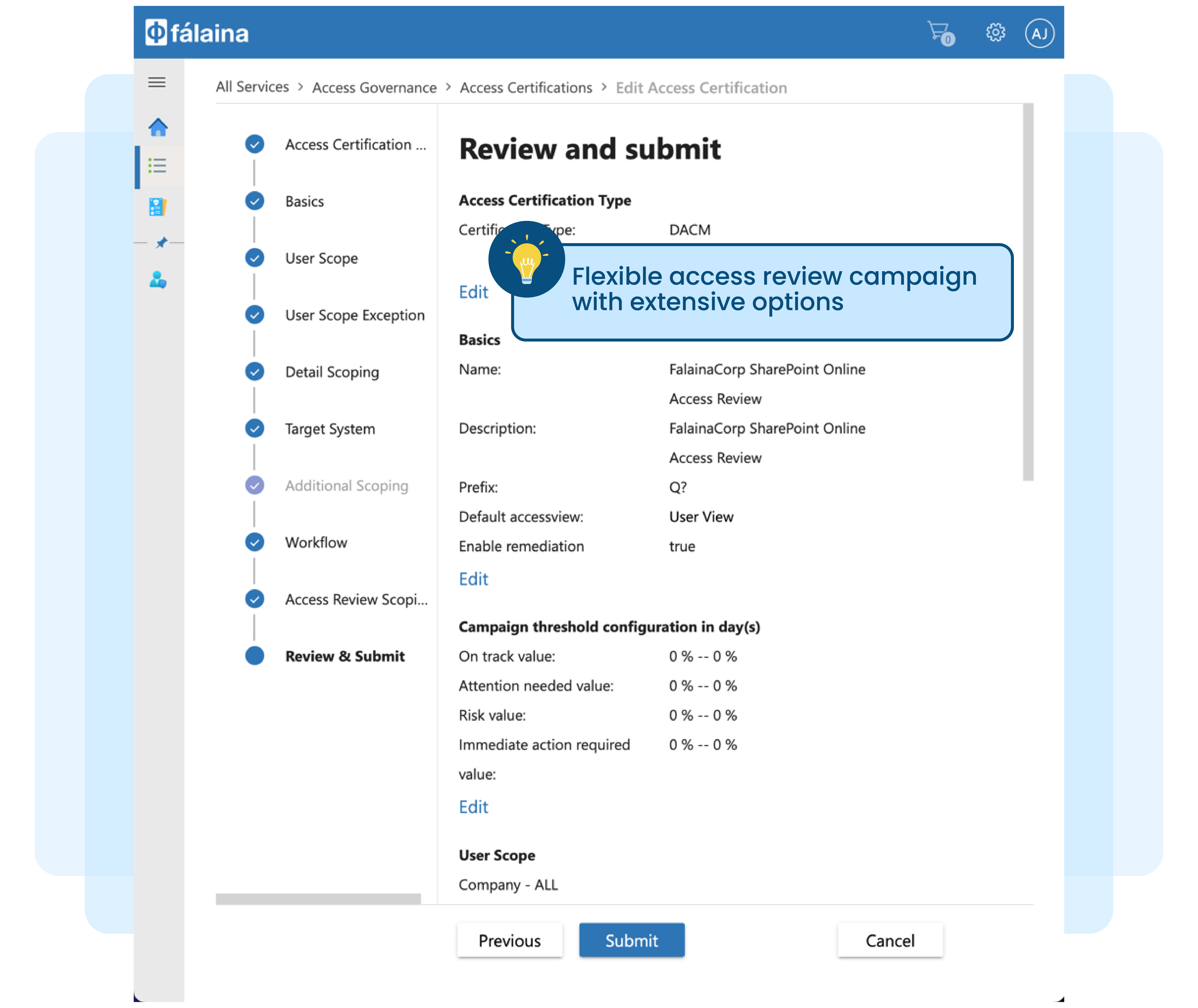
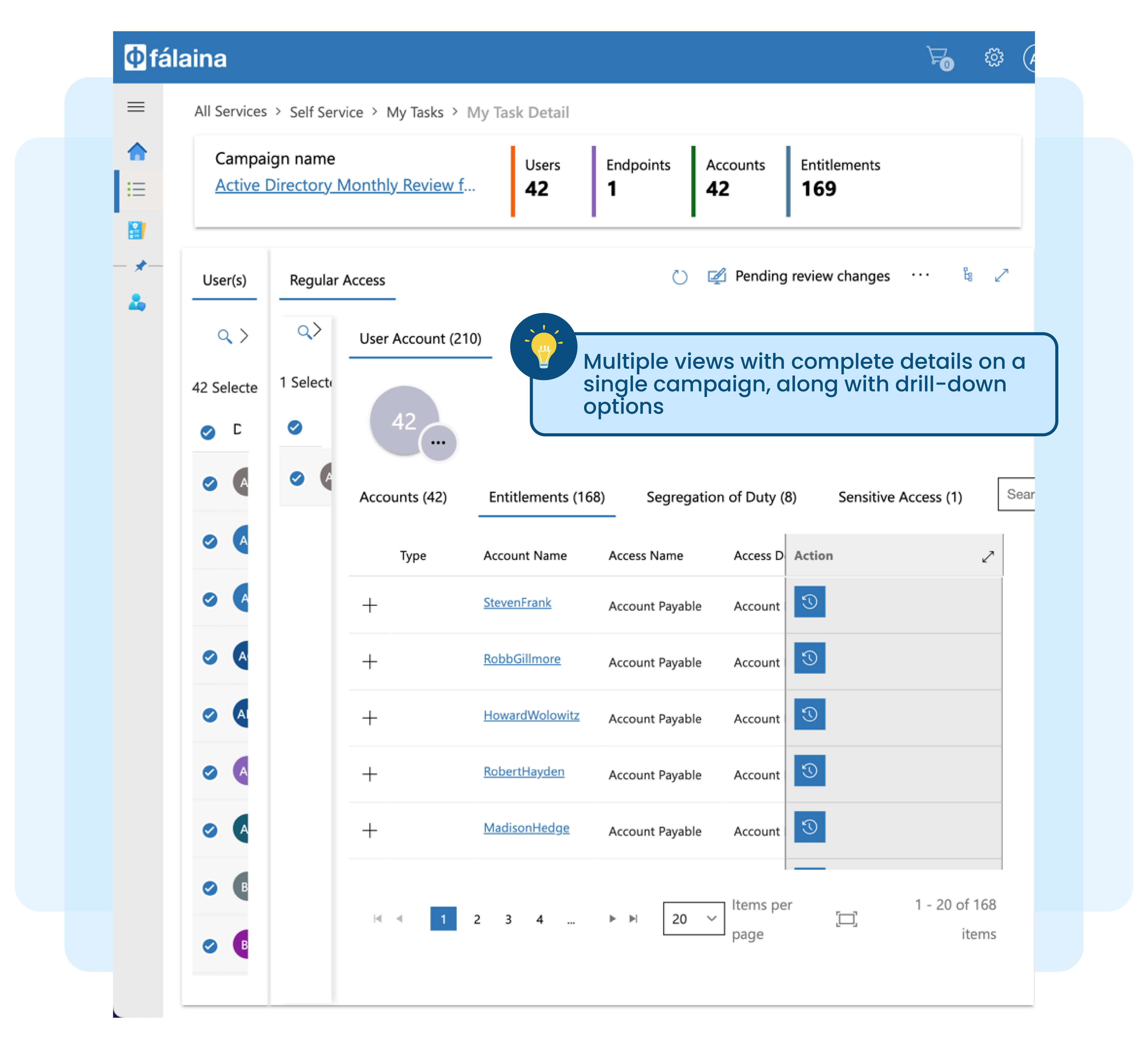
Access right review, attestation, or access certification (re-certification) are no longer new buzzwords in the industry. Most organisations today, in one way or another, need to perform user access review for critical applications to address regulatory or audit requirements.
Manually tabulating access matrix information exported from various target systems in spreadsheets, correlating them against users, and generating entitlement review reports is no longer practical.
Here’s why it’s not practical:
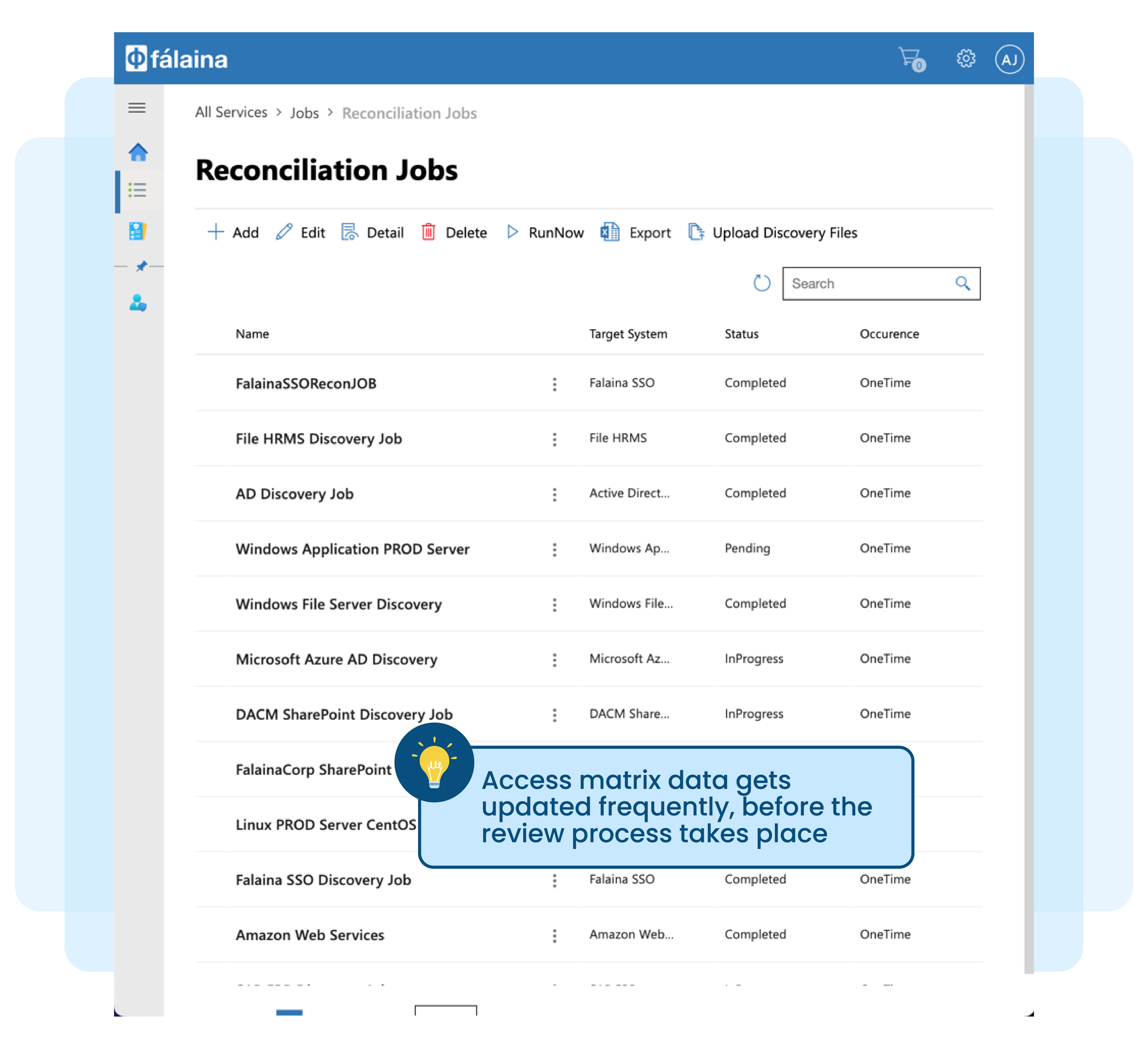
Access matrix data may not be updated on time for review
Not able to export beyond user accounts and group information
Normalising the data takes effort, and it is cumbersome and error prone
Manual review, sign-off, and remediation process is time-consuming
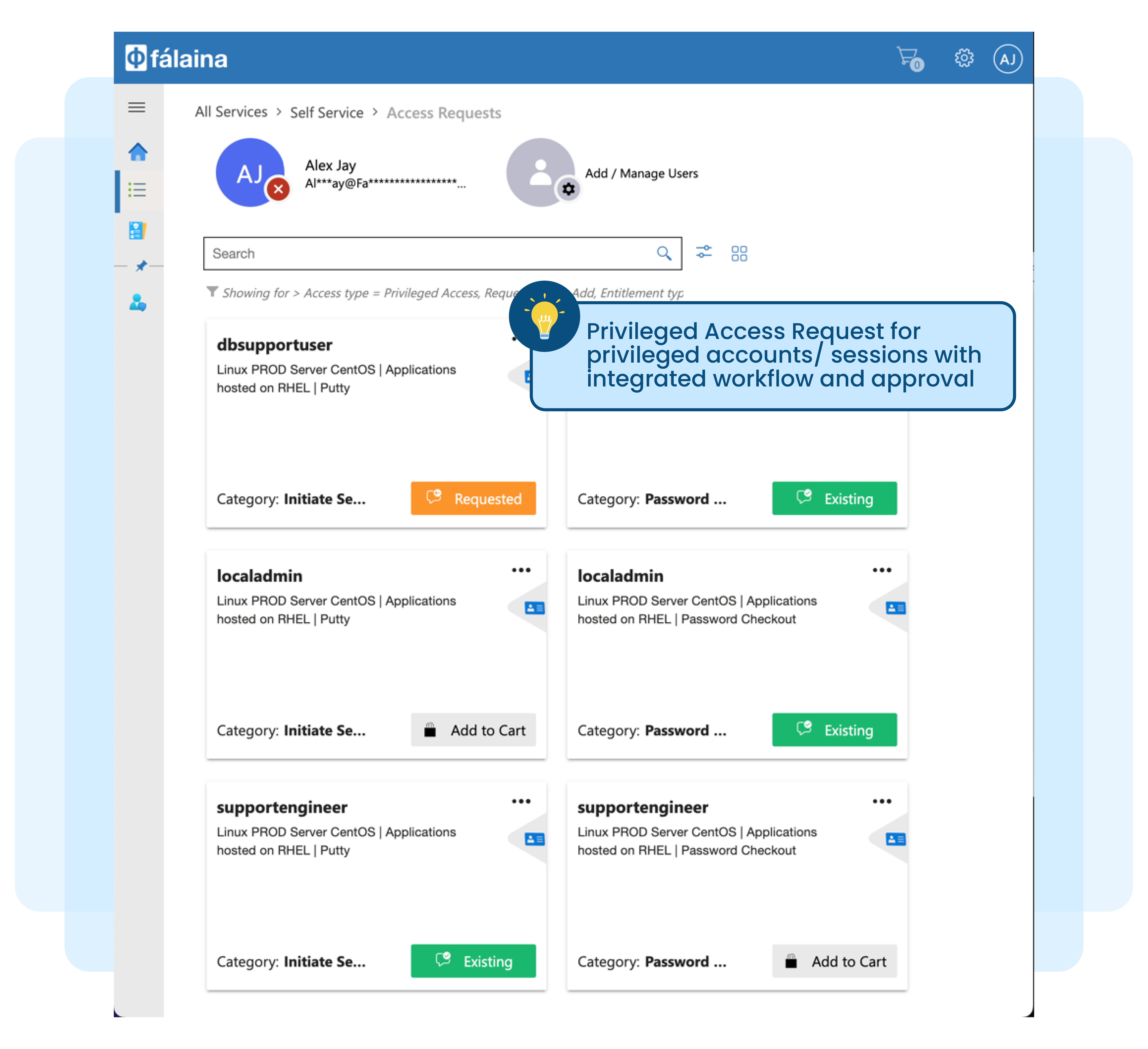
Paper-based or excel-based password check-out for Privileged Users
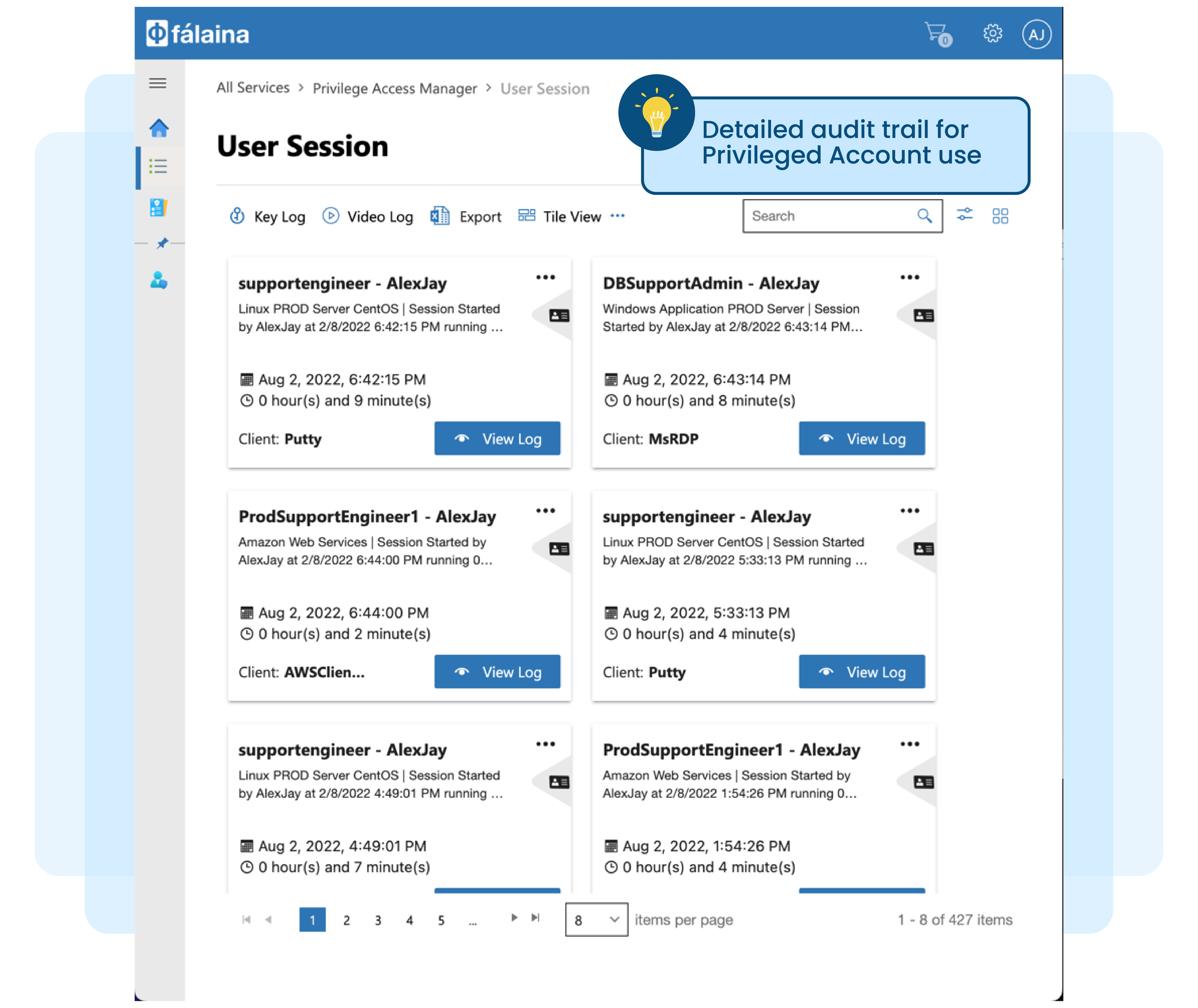
Historically, passwords for privileged and sensitive accounts across many target systems and applications have been kept in envelopes. When required for maintenance work, these passwords are requested manually and approved via email, and then the envelope with the password is given to the requestor. Today, instead of manual envelopes, passwords are kept in spreadsheets and managed in a similar manner.
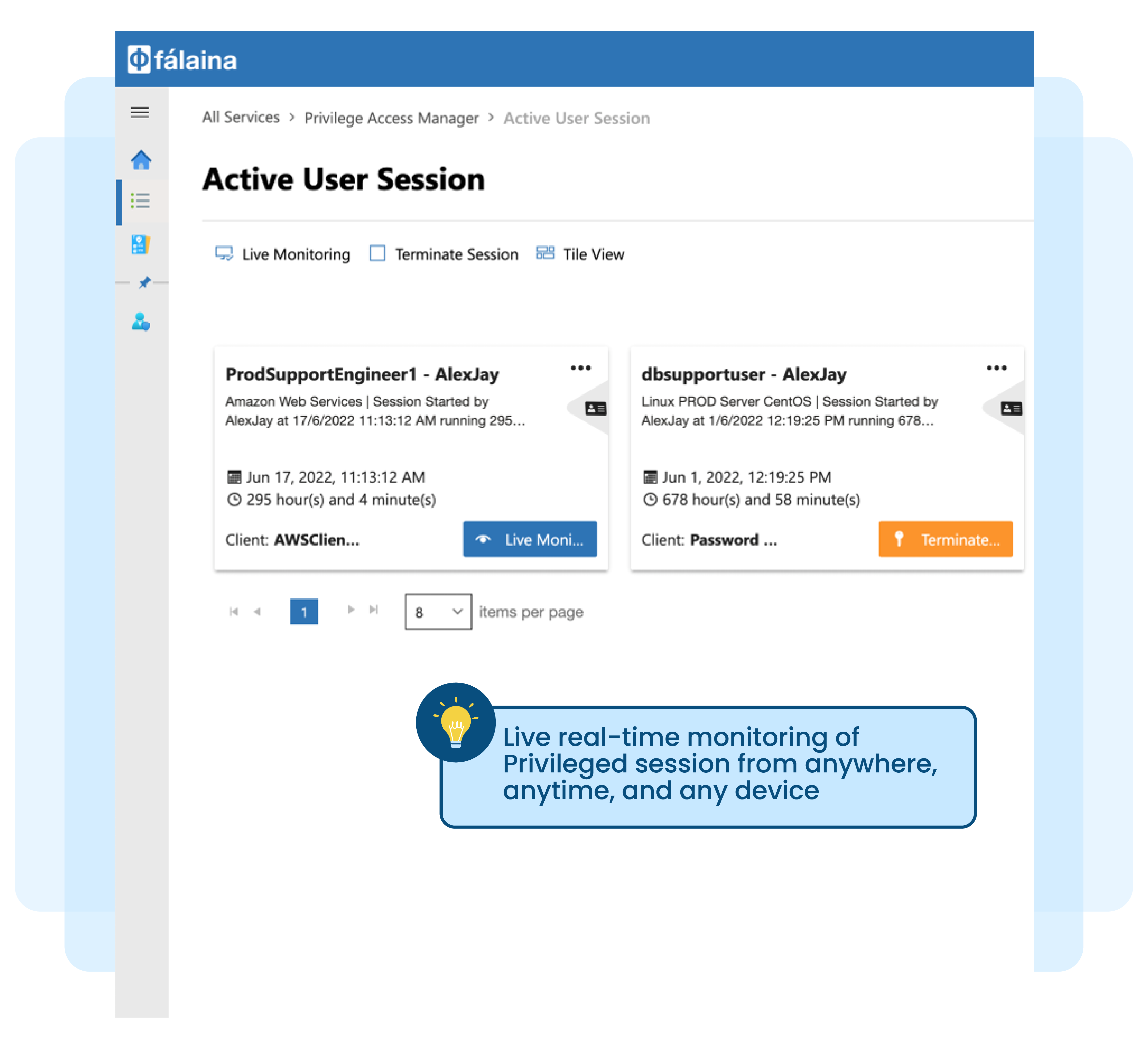
Managing privileged accounts manually or via spreadsheets, and having to rotate passwords and update spreadsheets on a daily basis is tedious, time-consuming and provides no audit trails for the actual usage of these privileged accounts.
Here are more reasons why paper-based or manual password check-out is not secure or practical:
No proper audit trail for privileged account requests, approval and usage
Lack of audit trail for the usage of privileged accounts
No remote monitoring capabilities if the work is done remotely
Lack of privileged account usage review
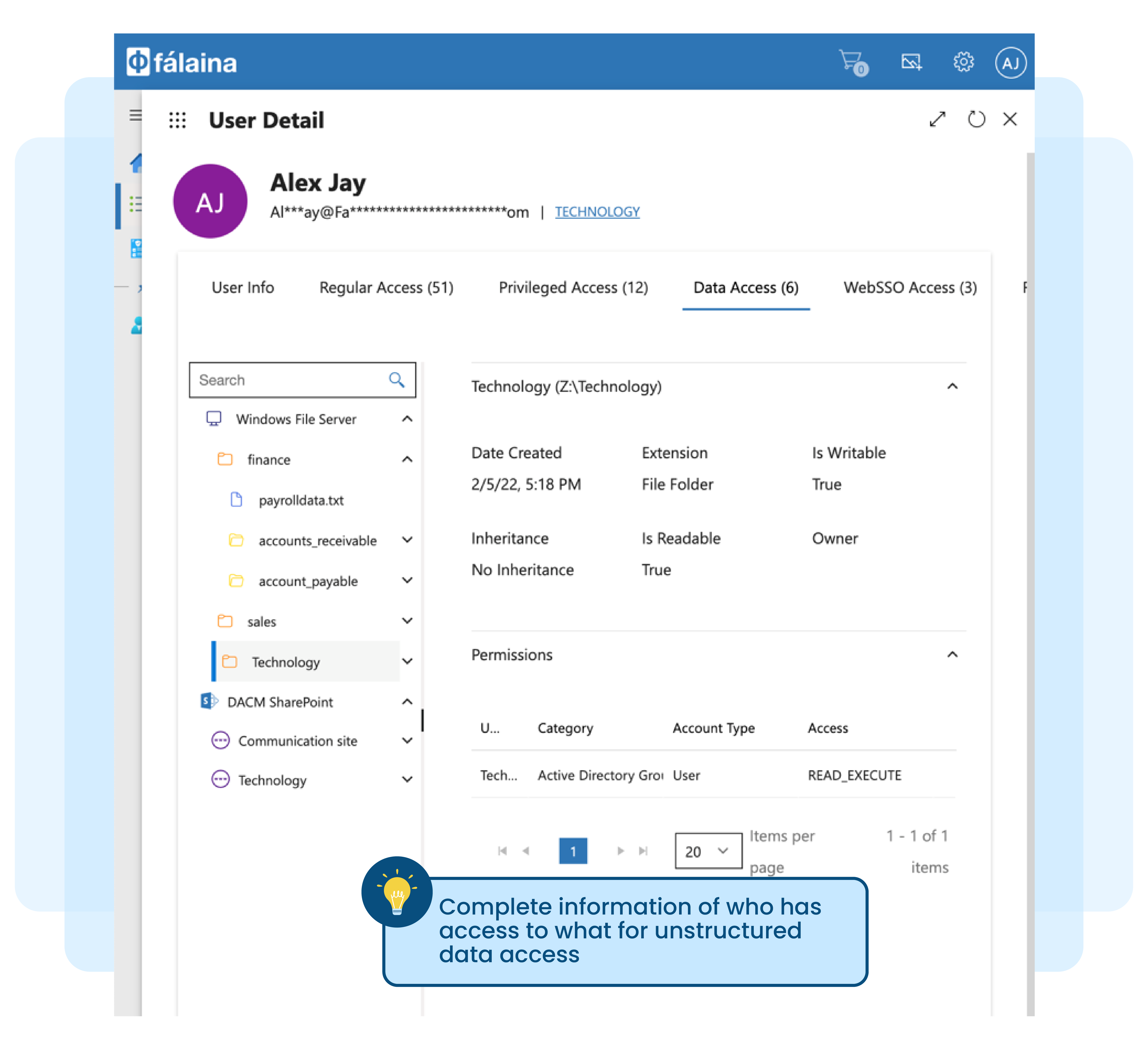
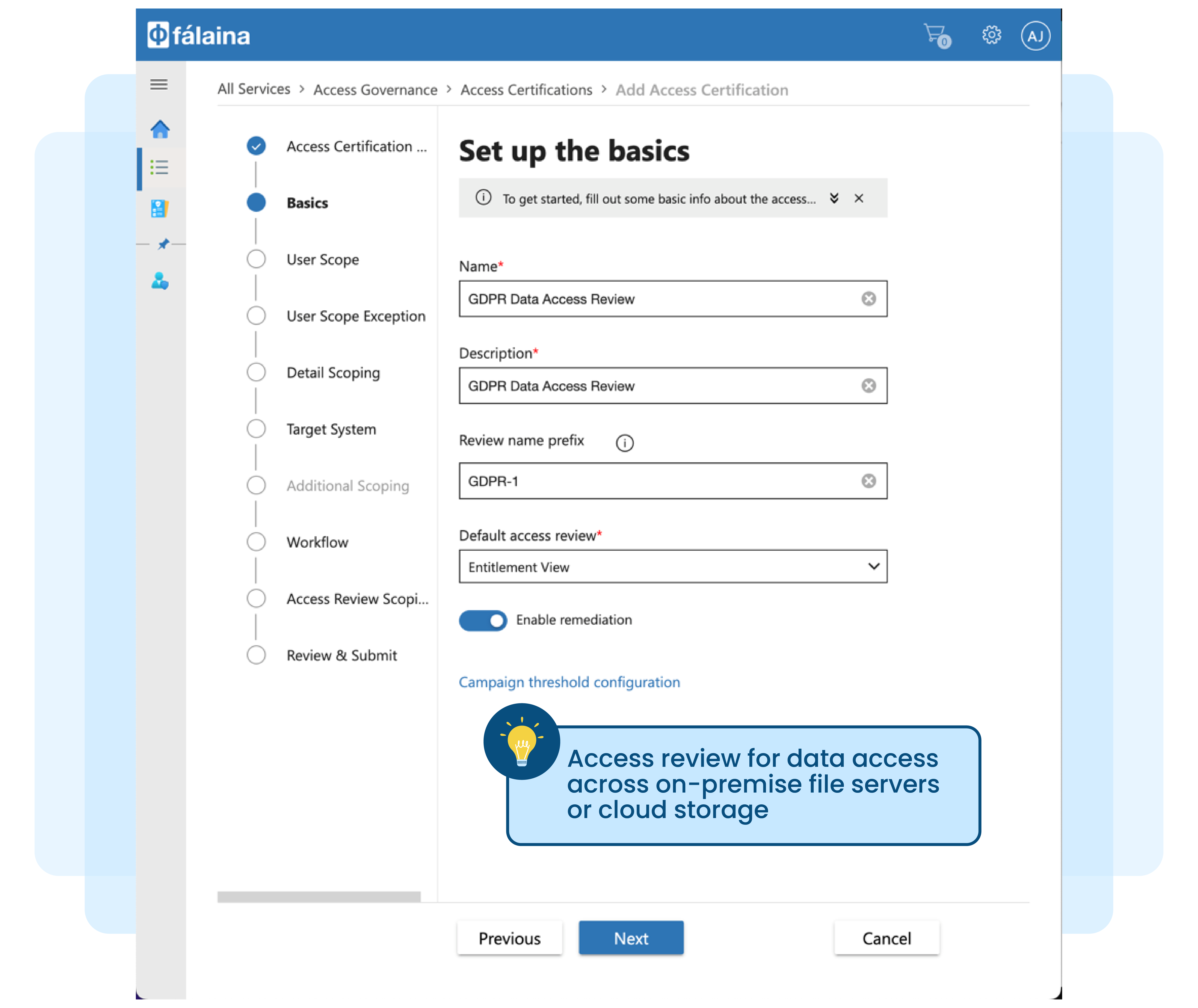
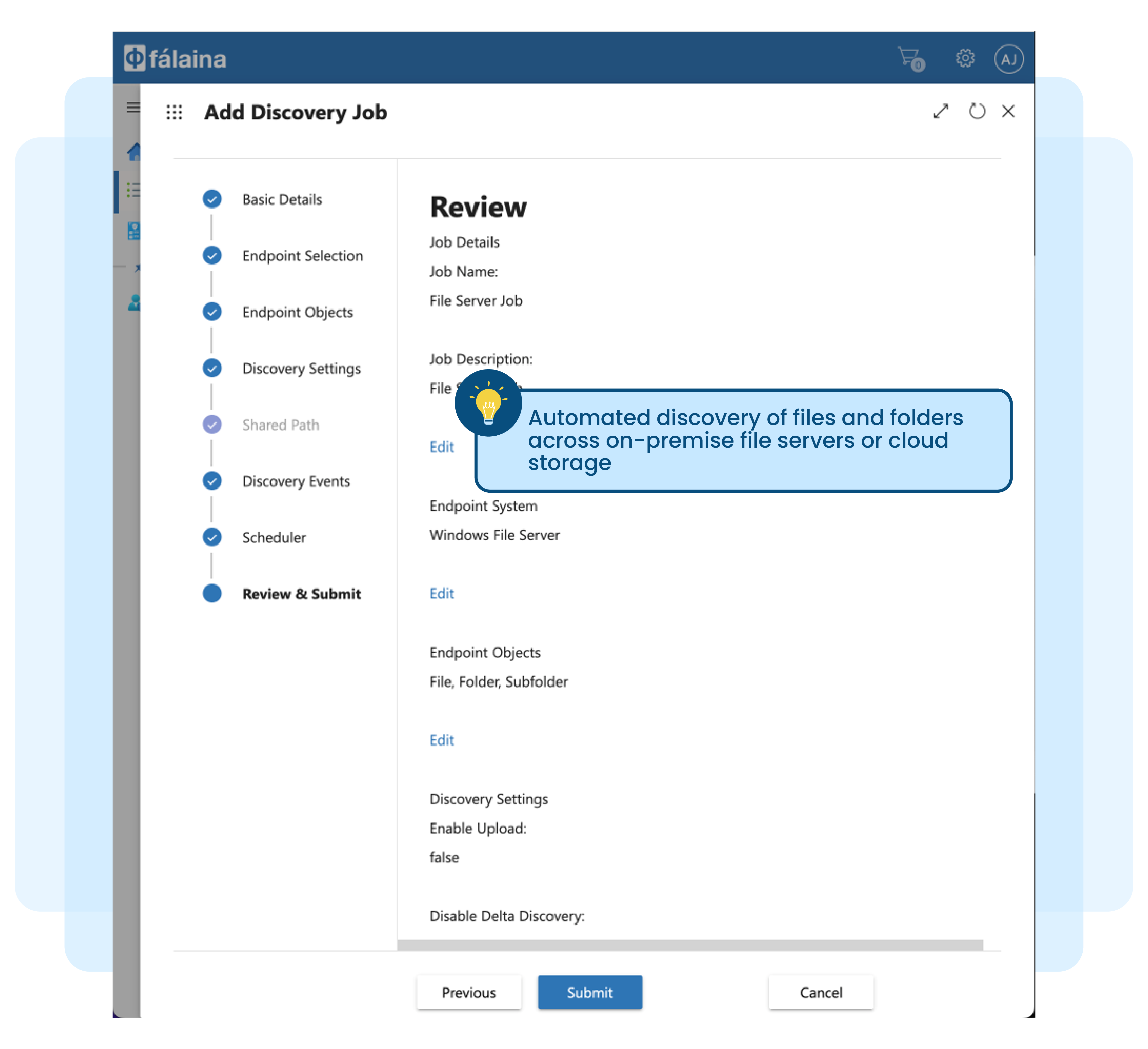
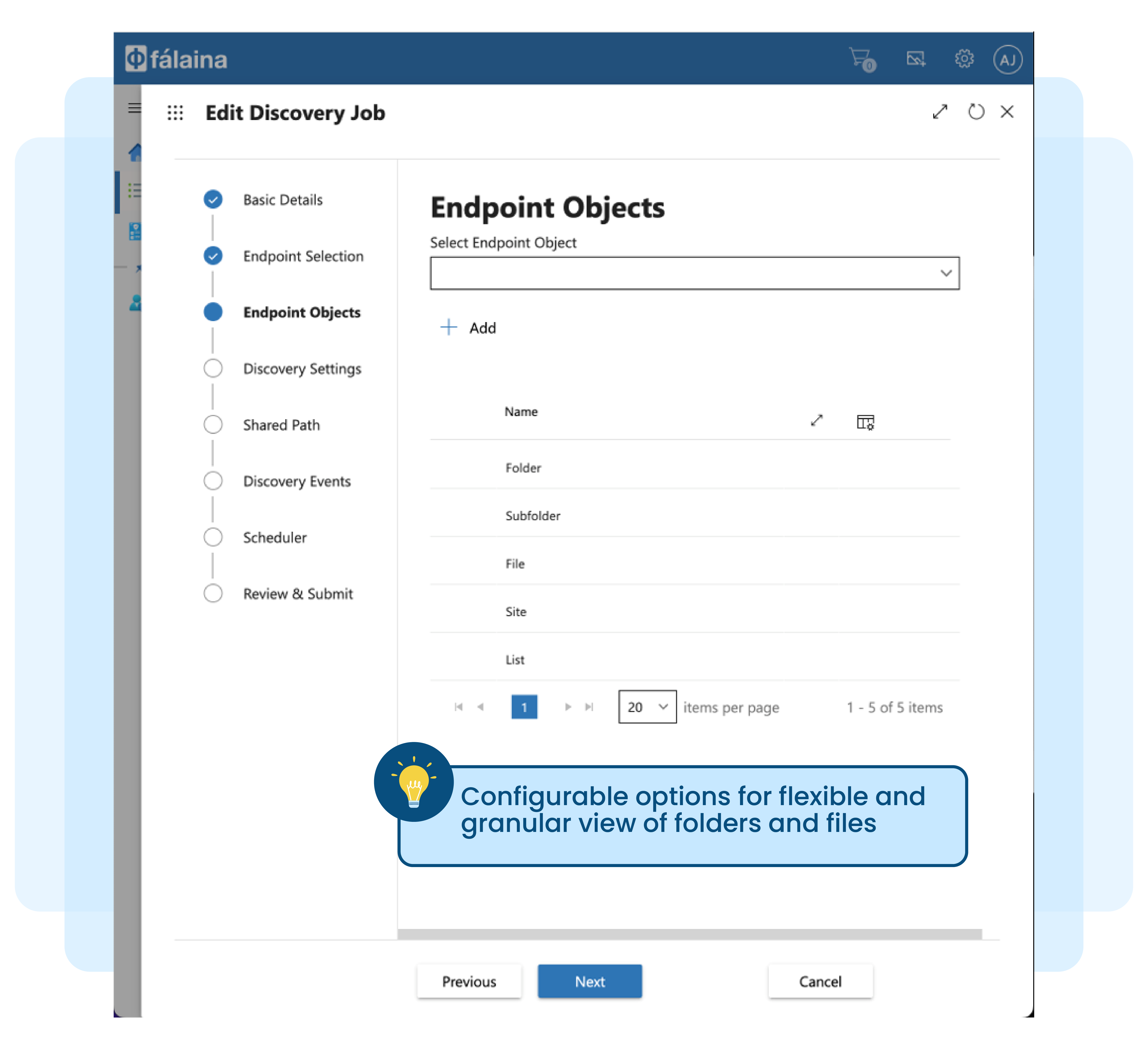
Managing file and folders manually not practical and tedious
Unstructured documents (files) and folders in Microsoft Windows File Servers or Microsoft SharePoint Servers grows significantly over time. Analysts estimate that these documents grow between 65-75 percent every year across all enterprises.
New files and folders are created on a daily basis and to make matters worse, each of these existing files are copied and shared. This creates a large number of duplicate files with different time-stamps and versions, making it difficult and complex to control access to unstructured data.
Here are other reasons why you may not be able to manually manage the folders and files in your enterprise manually: