


Falaina transforms identity security from fragmented tools to a unified, intelligent platform. Purpose-built for the modern enterprise, our platform simplifies complexity, cuts costs, and enforces Zero Trust access across your digital ecosystem

Round-the-clock identity defense with real-time threat detection and breach response.

Gain complete visibility into identities and access with AI-driven governance. Automate certifications, enforce policies, and stay audit-ready with ease.
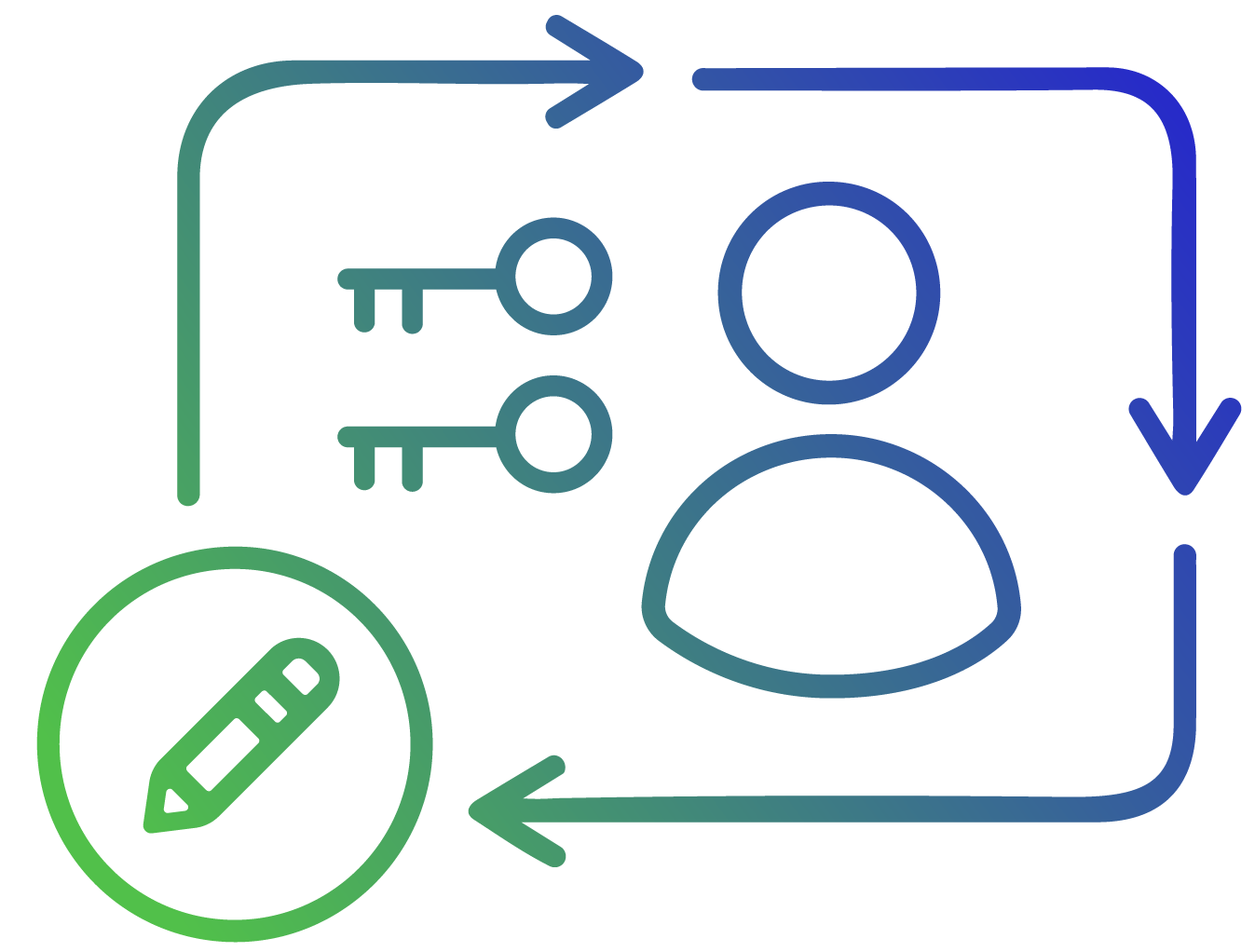
Automate onboarding, provisioning, and de-provisioning for human and machine identities. Eliminate orphan accounts, reduce errors, and enforce Zero Trust access.
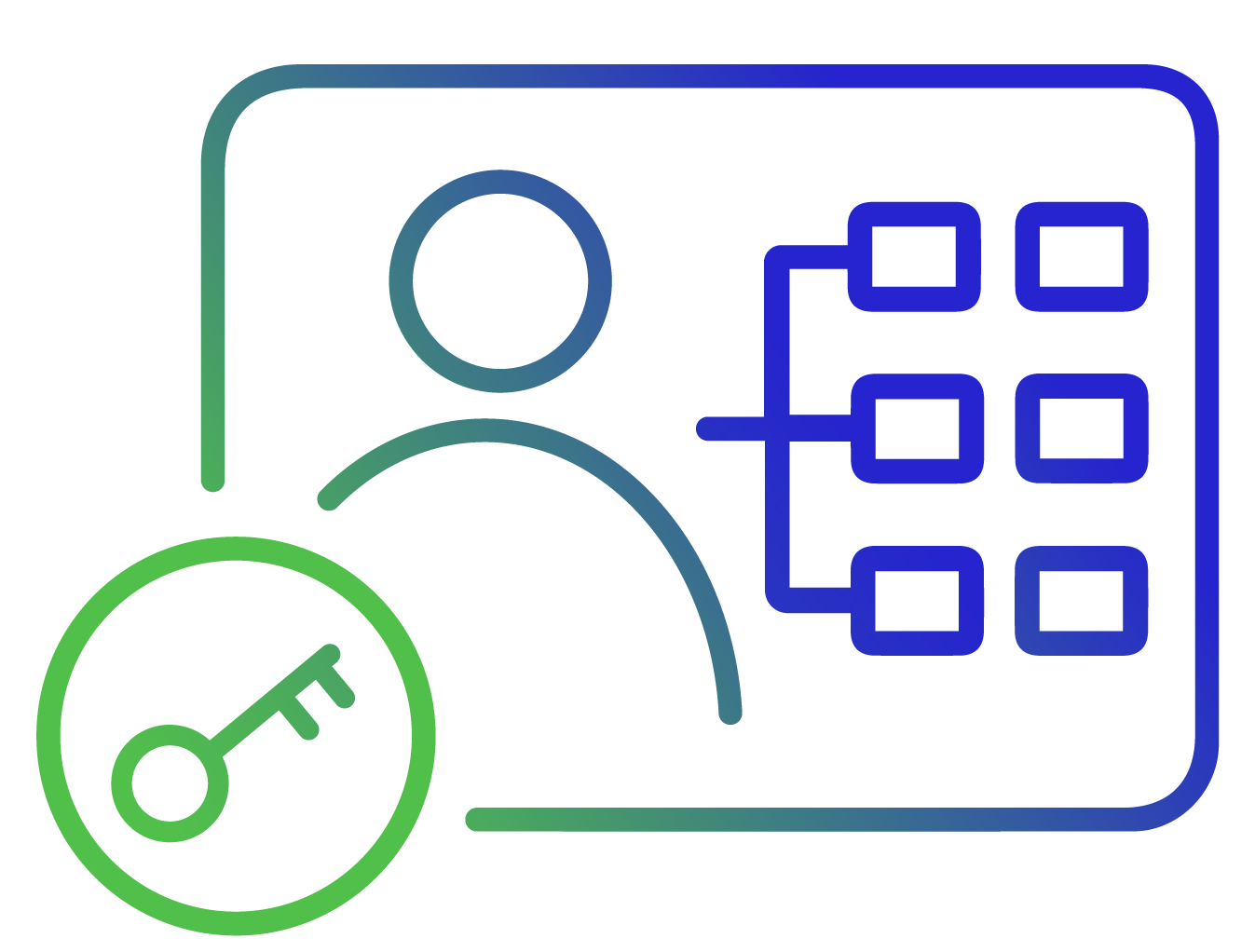
Simplify logins with seamless single sign-on and adaptive MFA. Strengthen security with risk-based access across cloud, SaaS, and legacy apps.

Stop credential theft with phishing-resistant, passwordless authentication. Enhance user experience with biometrics, passkeys, and adaptive MFA policies.
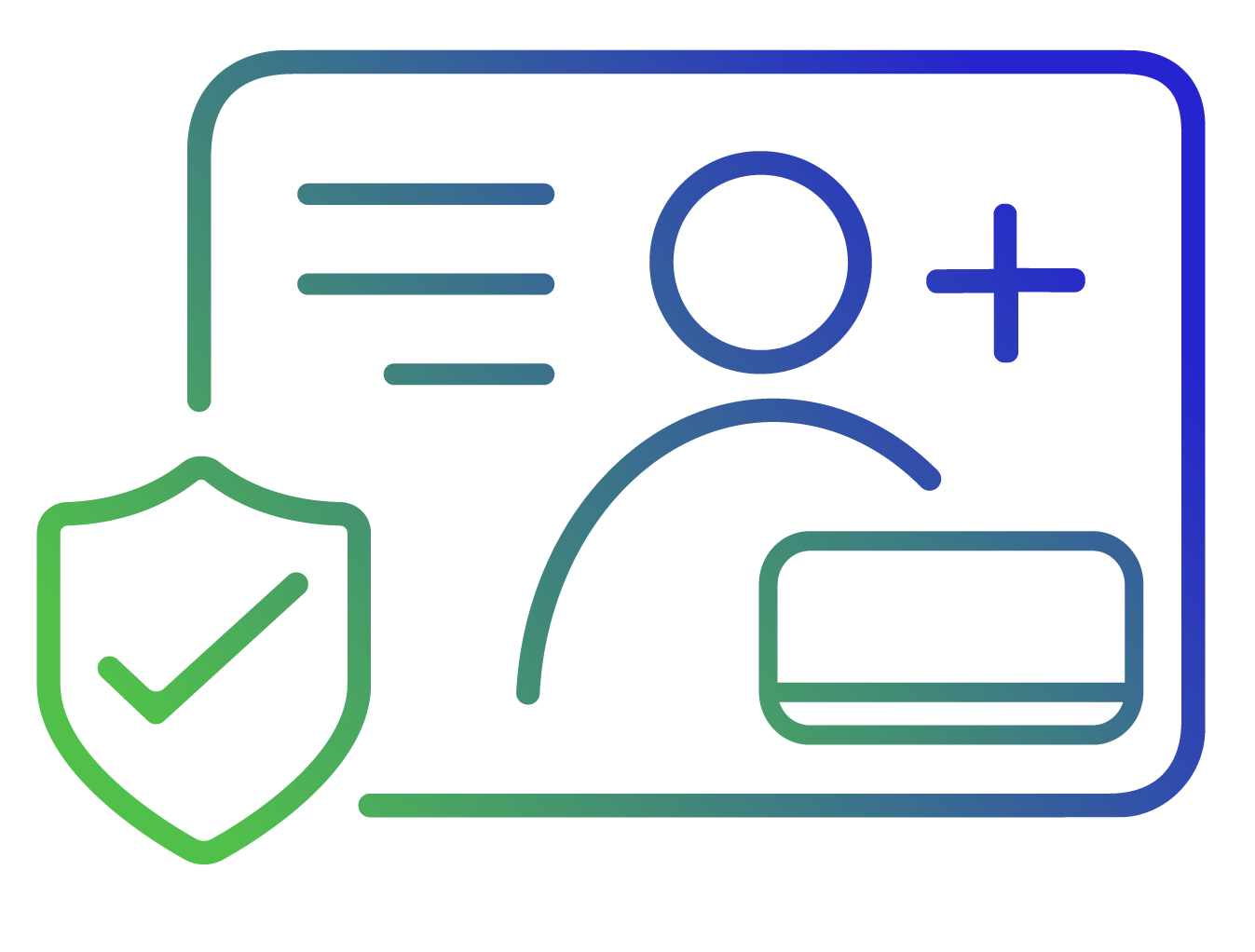
Secure admin and privileged accounts with JIT access and credential vaulting. Monitor sessions in real time and prevent insider or credential-based threats.

Gain visibility and control over unstructured data across cloud and hybrid systems. Automate reviews, enforce compliance, and protect sensitive information from misuse.



Falaina powers secure access and compliance for banks, hospitals, GLC and global enterprises.
Reduced audit preparation time by 60% through automated access certification, cutting down manual workloads. Falaina helps financial institutions strengthen regulatory compliance while minimizing operational risk.
Achieved a 70% reduction in unauthorised access to patient data with role-based controls and adaptive access policies. This ensures HIPAA compliance while protecting sensitive health records from insider and external threats.
Cut identity provisioning time by 75% with automated lifecycle management, improving workforce efficiency. Falaina also streamlines regulatory compliance, helping utilities maintain security across hybrid and legacy systems.
We provide out-of-the-box connectors that support integration with 70+ systems, including SAP, Oracle, Active Directory Azure, AWS, ServiceNow, Salesforce, and more. Beyond that, Fálaina Universal Connector Framework (UCF) provides seamless integration to non-standard applications with various protocol, including API, LDAP, SSH, Database and more.
Falaina Managed IAM Services offer 24/7 protection, onboarding automation, and compliance-as-a-service.

7030 Ang Mo Kio Avenue 5 #09-46, NorthStar AMK 569880, Singapore